In today’s digital world, building a secure web app is essential—requiring a security-first approach throughout development to protect data and ensure trust.
Why Web App Security Matters
Every day, thousands of web applications are compromised due to poor coding practices, misconfigured servers, or outdated components. Common attacks like SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF) can steal data, hijack sessions, and damage business reputations.
That’s why secure web app development should be part of your software architecture, not an afterthought.
Step-by-Step Guide to Building a Secure Web App
The first and most vital step in creating a secure web app is to clearly define the project scope and requirements. This phase lays the groundwork for both robust functionality and strong security, ensuring your app is built right from day one.
1. Define Project Scope and Requirements for a Secure Web App from Scratch
Start by clearly identifying the purpose of your application — who will use it, what problems it will solve, and what key features it must have. Alongside functional requirements, you should outline security requirements early in the process. This includes determining what sensitive data the app will handle, understanding potential threats, and deciding on necessary compliance standards (such as GDPR, HIPAA, or PCI-DSS).
Involving stakeholders, developers, and security experts from the beginning ensures that security is baked into the design rather than added as an afterthought. A well-defined scope helps prevent unnecessary features, keeps development on track, and ensures the final product meets both business goals and robust security standards.
2. Planning & Design Phase for a Secure Web App
The planning and design phase is the blueprint for your Secure Web App. At this stage, your primary goal is to build security into the architecture from day one rather than treating it as an afterthought.
Start by creating detailed wireframes and mapping out every user interaction. Identify where sensitive data will be stored, processed, or transmitted so that you can integrate security measures early. Choose a design approach that supports role-based access, minimal data exposure, and secure API integrations.
It’s also essential to select frameworks and architectural patterns that are known for strong security, such as MVC or microservices with container isolation. Include plans for implementing features like SSL/TLS encryption, multi-factor authentication, and secure session management.
By embedding security decisions into the design, you ensure that your Secure Web App remains robust against evolving cyber threats while still delivering a smooth, user-friendly experience.
3. Choose the Right Tech Stack

Selecting the right tech stack is one of the most important decisions when building a Secure Web App. Your choice of programming languages, frameworks, and databases will directly impact not only performance and scalability but also the overall security of your application.
A well-chosen tech stack ensures you can integrate modern security features, follow industry best practices, and maintain long-term flexibility as your app grows.
Key Considerations When Choosing a Tech Stack for a Secure Web App:
- Security Support: Opt for frameworks and libraries with strong built-in security features and regular updates (e.g., ASP.NET Core, Django, Laravel).
- Community & Documentation: Use technologies with active communities and well-documented security guidelines.
- Scalability & Performance: Ensure your stack can handle growth without compromising security measures.
- Compatibility with Encryption Standards: Choose tools that support SSL/TLS, secure hashing, and modern encryption algorithms.
- Database Security: Select databases with robust access control, encryption options, and audit logging.
By carefully selecting a tech stack with security in mind, you lay the foundation for a Secure Web App that is resilient, scalable, and compliant with best practices from day one.
4. Development & Security Best Practices

During the development phase, following security best practices is crucial to building a Secure Web App that protects user data and withstands cyber threats. Implementing strong coding standards, proactive security measures, and thorough reviews helps prevent common vulnerabilities like SQL injection, cross-site scripting (XSS), and data leaks.
Essential Development & Security Best Practices Include:
- Input Validation: Always validate and sanitize user inputs to avoid injection attacks and ensure data integrity.
- Use Parameterized Queries: Prevent SQL injection by avoiding direct concatenation of SQL commands and using parameterized queries instead.
- Follow OWASP Guidelines: Adhere to the Open Web Application Security Project (OWASP) Top 10 recommendations to address the most critical security risks.
- Implement Secure Session Management: Use secure cookies, set appropriate session timeouts, and protect against session hijacking.
- Enable HTTPS Everywhere: Ensure all data transmissions occur over encrypted channels to protect sensitive information.
- Apply Principle of Least Privilege: Grant the minimum necessary permissions to users and services to limit potential damage from breaches.
- Regular Code Reviews and Static Analysis: Conduct peer reviews and use automated tools to detect security flaws early.
- Secure Error Handling: Avoid revealing sensitive information in error messages which could be exploited by attackers.
By integrating these development and security best practices, you create a robust foundation for your Secure Web App, safeguarding it against evolving cyber threats and ensuring long-term reliability and trustworthiness.
5. Implement Strong Authentication & Authorization for a Secure Web App

One of the most critical steps in building a Secure Web App is implementing robust authentication and authorization mechanisms. These security layers ensure that only legitimate users can access your application and that each user can only perform actions permitted by their role.
Key Practices to Strengthen Authentication & Authorization:
- Multi-Factor Authentication (MFA): Add an extra layer of security by requiring users to verify their identity using multiple methods, such as passwords plus SMS codes or authenticator apps.
- Secure Password Policies: Enforce strong password requirements, including minimum length, complexity, and periodic changes, to reduce the risk of credential theft.
- Password Hashing and Salting: Never store passwords in plain text. Use strong hashing algorithms combined with unique salts to securely store user credentials.
- Role-Based Access Control (RBAC): Assign permissions based on user roles to limit access to sensitive features and data, minimizing the impact of compromised accounts.
- Session Management: Protect sessions with secure cookies, set appropriate expiration times, and invalidate sessions after logout or inactivity.
- OAuth and OpenID Connect: Leverage modern, standardized authentication protocols to securely manage user identity and enable single sign-on (SSO) capabilities.
- Account Lockout & Monitoring: Implement account lockouts after multiple failed login attempts and monitor suspicious activity to prevent brute force attacks.
By integrating these strong authentication and authorization strategies, your Secure Web App will effectively protect user identities and safeguard sensitive data, building trust and compliance with security standards.
6. Testing & Quality Assurance for a Secure Web App

Ensuring your Secure Web App performs reliably under all conditions is critical. Testing and quality assurance (QA) are essential phases that help identify vulnerabilities, bugs, and performance issues before your app reaches users.
Key Testing & QA Practices for a Secure Web App:
- Automated Testing: Implement unit tests, integration tests, and end-to-end tests to continuously verify that individual components and their interactions work correctly.
- Security Testing: Conduct vulnerability scans, penetration testing, and static application security testing (SAST) to uncover and fix security flaws early.
- Performance Testing: Check how your app performs under load to prevent crashes and bottlenecks that could expose security risks.
- Regression Testing: Ensure that new code changes don’t break existing features or security measures.
- Continuous Integration (CI): Integrate testing into your CI pipeline to automate quality checks and catch errors immediately after code commits.
- User Acceptance Testing (UAT): Involve end-users or clients to validate the app meets business needs and usability standards.
- Code Reviews: Perform peer reviews focused on both functionality and security to maintain high-quality standards.
- Bug Tracking & Reporting: Use tools to log, prioritize, and fix issues efficiently, maintaining transparency in the development cycle.
By rigorously testing your Secure Web App throughout the development lifecycle, you ensure robustness, reduce vulnerabilities, and deliver a trusted product that users can rely on.
7. Data Encryption & Secure Communication
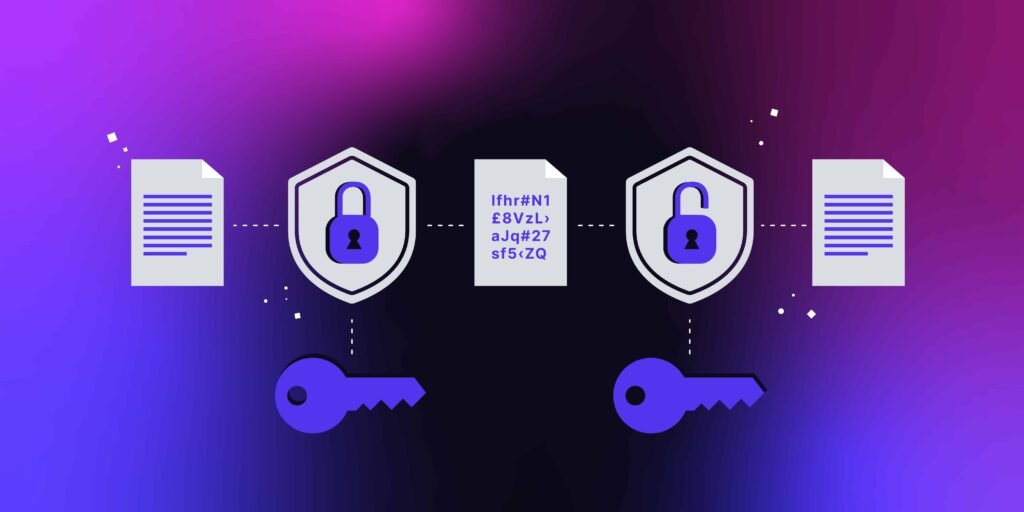
Protecting data both at rest and in transit is fundamental when building a Secure Web App. Data encryption ensures that sensitive information remains confidential and safe from unauthorized access or interception.
Key Aspects of Data Encryption & Secure Communication:
- Encryption at Rest: Use strong encryption algorithms (such as AES-256) to secure databases, files, and backups, preventing data breaches even if storage is compromised.
- Encryption in Transit: Implement HTTPS with TLS (Transport Layer Security) to encrypt data exchanged between the client and server, protecting it from eavesdropping or man-in-the-middle attacks.
- Secure APIs: Ensure all API communications are encrypted and authenticated to prevent unauthorized data access.
- Use of Certificates: Obtain and regularly update SSL/TLS certificates from trusted certificate authorities to establish secure connections.
- Key Management: Properly manage and store encryption keys using secure vaults or hardware security modules (HSMs) to prevent unauthorized key access.
- End-to-End Encryption: For highly sensitive applications, consider end-to-end encryption where data is encrypted on the client side and only decrypted by the intended recipient.
- Regular Audits: Continuously audit encryption protocols and configurations to ensure they meet the latest security standards.
By implementing strong data encryption and secure communication practices, your Secure Web App will maintain data privacy and build trust with users, safeguarding your app against cyber threats.
8. Deployment & Maintenance for a Secure Web App

Deploying your Secure Web App properly and maintaining it consistently is crucial to ensure ongoing security, performance, and reliability. A smooth deployment process combined with proactive maintenance helps protect your app against vulnerabilities and downtime.
Key Considerations for Deployment & Maintenance:
- Hardened Server Environment: Deploy your app on secure servers with up-to-date OS patches, firewall configurations, and minimized open ports to reduce attack surfaces.
- Automated Deployment Pipelines: Use CI/CD tools to automate deployment, ensuring consistent, error-free releases with integrated security checks.
- Backup & Recovery: Implement regular automated backups and a disaster recovery plan to prevent data loss and quickly restore service after failures.
- Security Patching: Keep all software components, libraries, and dependencies up to date with the latest security patches to protect against emerging threats.
- Monitoring & Alerts: Set up system and application monitoring to detect unusual activities, resource issues, or performance bottlenecks early.
- Access Controls: Restrict deployment permissions to authorized personnel only, and use role-based access controls for management.
- Documentation & Change Logs: Maintain thorough deployment documentation and change logs for transparency and easier troubleshooting.
By prioritizing robust deployment and diligent maintenance, your Secure Web App remains resilient against security risks and ensures a reliable user experience over time.
9. Continuous Monitoring & Incident Response

Ensuring your Secure Web App stays protected requires continuous monitoring and a well-prepared incident response plan. Detecting threats early and responding quickly can prevent minor issues from becoming major security breaches.
Why Continuous Monitoring Matters:
- Real-Time Threat Detection: Constantly track unusual activity, suspicious logins, or performance anomalies that could indicate attacks.
- Proactive Vulnerability Management: Identify weaknesses before they are exploited, keeping your app’s defenses up to date.
- Compliance Assurance: Maintain audit trails and logs required by security standards and regulations.
Incident Response Essentials for a Secure Web App:
- Preparedness: Develop a clear incident response plan outlining roles, responsibilities, and communication channels.
- Rapid Containment: Quickly isolate affected systems to minimize damage and stop the spread of attacks.
- Thorough Investigation: Analyze the root cause to prevent future incidents and patch vulnerabilities.
- Recovery & Restoration: Safely restore systems and data while ensuring the app’s security posture is improved.
- Post-Incident Review: Document lessons learned and update security measures accordingly.
By integrating continuous monitoring with a robust incident response strategy, you safeguard your Secure Web App against evolving threats, ensuring resilience and user trust.
10. Regular Updates & Security Audits for a Secure Web App

Maintaining a Secure Web App doesn’t stop after deployment. Regular updates and thorough security audits are critical to keeping your application resilient against new and emerging threats.
Why Regular Updates Are Vital:
- Patch Vulnerabilities: Software libraries and frameworks frequently release patches for security flaws. Keeping your app updated ensures these weaknesses are addressed promptly.
- Stay Ahead of Threats: Cyber attackers constantly evolve their tactics. Regular updates help your app defend against the latest vulnerabilities and attack vectors.
- Improve Performance: Updates often include performance enhancements that keep your app running smoothly and securely.
The Importance of Security Audits:
- Comprehensive Risk Assessment: Periodic audits identify hidden vulnerabilities and weaknesses that automated tools might miss.
- Compliance Verification: Audits ensure your app meets industry security standards and regulatory requirements.
- Continuous Improvement: Findings from audits guide your team to implement stronger controls, reducing future risks.
Best Practices for Ongoing Security:
- Schedule automated and manual security checks regularly.
- Update dependencies, plugins, and third-party integrations promptly.
- Use penetration testing to simulate real-world attacks.
- Monitor audit reports and act on recommendations swiftly.
By committing to regular updates and security audits, you ensure your Secure Web App remains robust, trustworthy, and compliant—safeguarding both your business and users over time.
Power Soft – Your Secure Development Partner
At Power Soft, we don’t just write code — we build secure digital solutions that scale with your business.
Our Secure Development Expertise:
- Custom Web Applications using ASP.NET Core, Angular, React
- Business Automation & ERP Solutions with role-based security
- Cloud Integration & Data Analytics using Azure, AWS, Power BI
Final Thoughts: Secure by Design, Not by Patch
Security isn’t a feature. It’s a mindset. By embedding security practices from the start, you reduce risk, protect your users, and build trust in your application.
📞 Ready to Build a Secure Web App?
Let’s protect your vision with enterprise-grade security.
Contact Power Soft today for a FREE consultation:
📧 Email: contact@powersoft.agency
🌐 Website: www.powersoft.agency/about
📞 Call & WhatsApp 1: +1 561-556-0226
📞 Call & WhatsApp 2: +88 01966 773464